In cybersecurity, the difference between a small event that requires minor investigation and a massive data breach can simply boil down to how strong the integration is between two of the often dozens of tools an organization deploys to maintain and monitor their security posture. This is further complicated by some organizations that use tools that are managed by separate teams, such as the desktop A/V and detection agent that the IT or application group manages instead of the security team.
Recently, a customer event highlighted the strength of Juniper’s Security Director Policy Enforcer in a key use case for this type of situation. The desktop team was unavailable during an incident discovered by the security operations center (SOC) that required immediate action. In the case of active malware and ongoing attacks, dwell time of the attacker can often be directly correlated to the impact of the incident and potential breach.
The customer will remain anonymous; however, their use case is not unlike the organizational structure of many businesses around the world today. There is a network and operations team, a security group that works alongside them and a variety of other disciplines found in a typical enterprise to support many independent divisions and locations. Each site is loosely governed by a common policy structure with the WAN access methods in addition to security rules at the edge of each network being centrally managed.
However, the desktop applications – and, notably, the antivirus applications – remain under each division’s charter. As a result, the choice of agent and management of them is determined by the locally governed IT function. This allows the SOC to centrally monitor all events and traffic between every department and ensure the overall infrastructure is protected.
Identifying the Incident
With Juniper SRX Series firewalls and Advanced Threat Prevention capabilities deployed, the SOC identified that a host within a division’s environment was infected by malware via command and control requests and application behavior indicators. Specifically, this involved network scans for additional susceptible hosts (an investigation later determined the user had been phished and had unknowingly downloaded the malware while off the VPN on their home network).
With Juniper’s Advanced Threat Prevention solution, the malware command and control connection and network behavior were rapidly identified and the severe alert raised. However, without desktop or agent access to the host itself, the SOC would have little recourse but to keep trying to reach the local IT team. Otherwise, they would be faced with more drastic action choices up to (and potentially including) the temporary WAN link severance.
In this customer environment, Juniper Security Director and Policy Enforcer components were actively managing all of the Juniper infrastructure and integrated with the Juniper EX3400 switches deployed throughout the environment. During the incident, when the ATP Cloud service had identified the command and control (C&C) traffic, it associated the host, host port and a number of other critical identifier elements with the alert. It also applied a critical risk level. Within the UI of Security Director, all of this information was provided to the SOC team, along with the tools to surgically disconnect only that host from the environment via a Policy Enforcer component.
This instance was part of our Infected Host feed workflow, where a host is identified by threat level or risk. It was then associated with an active indicator of compromise, after which the infected host identity passed via the Infected Host feed over to the Security Director Policy Enforcer (PE) instance and remediation was executed. For a threat of this severity, the customers’ PE instance was configured to send an execution command to the switch and disconnect the host port itself.
In the graphic below, the screen capture represents an example of compromised hosts, along with the malware that was identified on specific hosts (and file type) within the Advanced Threat Prevention console.
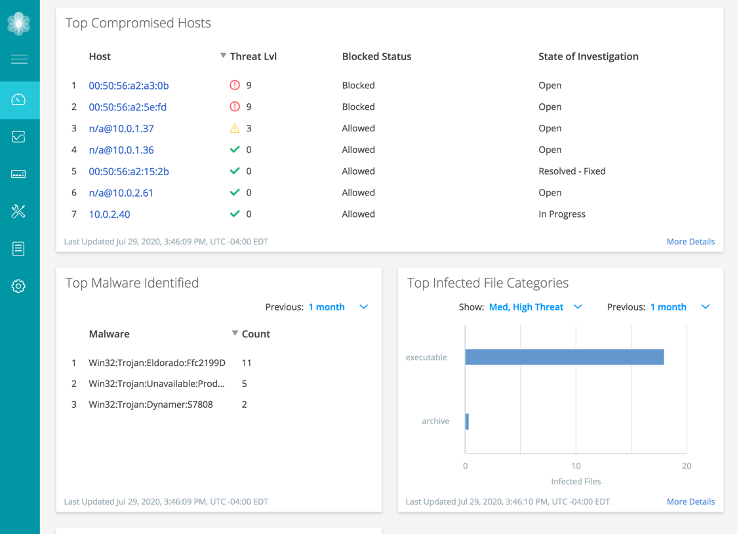
The Policy Enforcer control or mitigation capability is just as effective on multivendor switches, routers and other infrastructure technologies as it was in this case on the Juniper switches. The key is that the right details are captured and associated with the host detail, in addition to enabling security ops personnel to quickly identify the policy status. From there, they set the investigation status so that other members of the investigation team can see the policy control that is in effect and clear the flag or take additional action, once resolved.
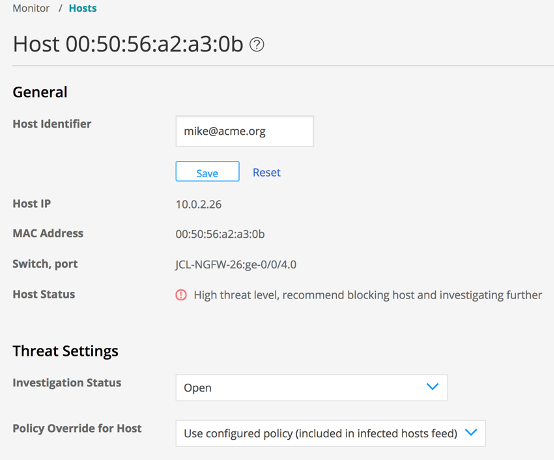
The customer is still negotiating for the governance of the desktop A/V (and remaining security controls) within that division. Until then, Juniper Connected Security provides peace of mind that when a security incident occurs on a device or node they do not have direct governance of, they have the tools to assist in the protection of the environment and, ultimately, prevention of a more dire outcome.

























