The Kronos banking malware family was first known to be sold in the underground market in 2014. It surfaced again in mid-2017 after being dormant for some time. Then, in April 2018 we saw a resurgence of Kronos in new avatar Orosis. Some security vendors reported its presence in September 2018.
IOC’s
MD5: F085395253A40CE8CA077228C2322010
sha1:0B2A845E4EAF1505634B6E3BD40D47E94FD630FE
Kronos Attack Vectors:
Kronos is known to be distributed via various attack vectors, some versions known to spread through malvertising. Some have also spread using phishing emails containing document attachments containing macros that can then download the malware. Some of the attachments are also known to exploit a Microsoft Word vulnerability CVE-2017-11882.
Packer Evolution:
The initial versions of Kronos were known to use the well-known process hollowing technique. This is a technique frequently used by malware to impersonate legitimate processes. The malware launches a legitimate process and replaces the the code in runtime with a malicious payload. The latest version of this seems to use a new technique very similar to Doppelgänging already analysed in this Malwarebytes blog. The concept was described at Black Hat 2017.
Technical Description of the Payload:
The malware creates a copy of itself into app data and maintains persistence by creating a run entry in the registry. HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
It uses a technique called Web-injects. Web Inject is a man-in-the-browser-attack, a technique by which malware can manipulate the web page in the browser and display a custom web page. As an example, if a banking website displays username and password in the login page, the malware can modify the web page on the client side to have an additional field to enter ATM pin. Thus the end user gets fooled into thinking that the the original bank site is asking for their ATM pin. This kind of attack is effective against sites using SSL encryption too as opposed to man-in-the-middle attacks which only work on unecrypted traffic (unless a malicious certificate is inserted in the browser and accepted by the user). Kronos web-injects are very similar to those of the infamous Zeus family.
The trojan is then modularized and uses a configuration file which makes it easier to update the malware.
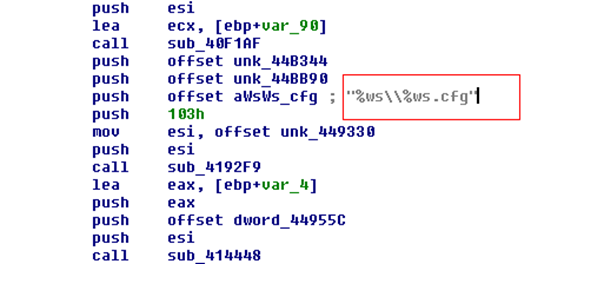
The configuration file is very much similar to Zeus. The configuration file has specifications of the web injects. It mentions what modifications (html code injections) need to be done to the web page of a certain banking website on the victim’s machine. The Zeus type of configuration file usually has strings like set_url,data_before,data_after,data_inject,data_end. These strings indicate fields in the configuration file. These fields tell where and what to be injected.
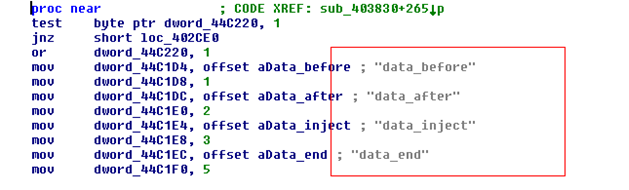 string related to zeus style config file
string related to zeus style config file
- set_url field specifies the target UR
- data_before and data_after are used to indicate the location in the web page when malicious code is injected
- data_inject and data_end used enclose the content that needs to be injected
Some versions of Kronos are also known to steal and inject code into social networking sites.
Unpacked versions of Kronos can be identified easily as they have the “Kronos” string in them.
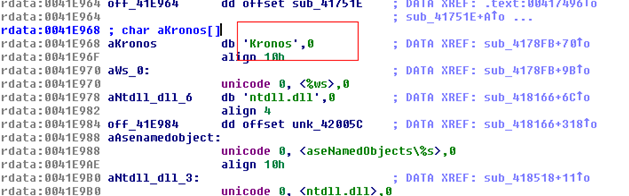
Latest versions are known to use TOR network and also have VNC modules.
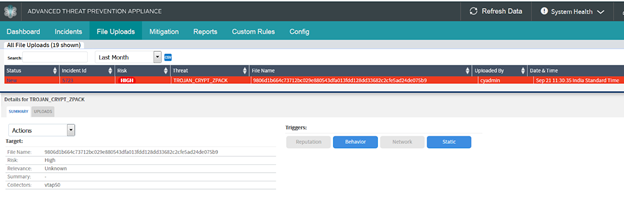
Detection
Both Juniper Sky ATP and Juniper ATP Appliance on-prem solutions detect this threat as seen in the screenshots below. Keeping security solutions up-to-date can keep the customer protected against this type of threat, as well as others.