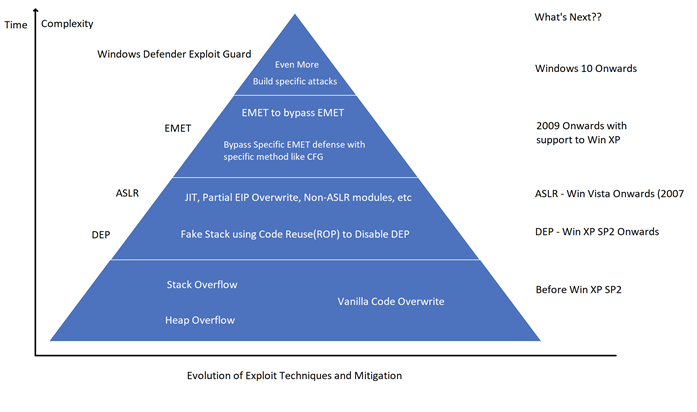
Windows has been a target of hackers for a long time. The reason is simple: it is the OS with the largest deployment footprint around the world. Hackers discover vulnerabilities in Windows OS software as well as the various software that support Windows OS. Exploits as well as exploit mitigation techniques have evolved over the years. Over time, the targeted exploit has shifted from server applications to desktop applications. Adobe Flash has been a favorite target for the past seven to eight years. In this article we will talk about the exploits and their mitigation techniques on Windows.
Exploits are meant to compromise the system by taking advantage of a vulnerability in the program. Before moving ahead, let us first discuss how hackers find a vulnerability in an application.
Common vulnerability discovery techniques:
Fuzzing: This is a common way to test for vulnerabilities. The hackers provide a large range of inputs for the target software and observe for any unexpected behavior. For browsers, a lot of HTML files are created as an input. If the vulnerability has not been seen earlier, it is called a zero day vulnerability.
Patch diffing: This is a technique by which an update in software is compared with an old version. Windows used to update its software by means of DLLs. Hackers can compare the old and new DLL to find out what code is patched. After this, they can analyze it to find out if the old code is vulnerable. Hackers write the exploit to take advantage of the vulnerability assuming that not everybody would have applied the new software patch immediately. These kind of exploits are called one day exploits.
Leaks:
There are certain organizations that discover zero day vulnerabilities for commercial software testing. Hacking Team was one of these. Hacking Team exploits were leaked in 2015. Eternal Blue is also one of such infamous exploits that contributed to the spread of WannaCry and Petya malware
Types of Vulnerabilities and Windows countermeasures
Buffer Overflow vulnerabilities: These kinds of vulnerabilities occur when a program doesn’t check the boundary of user-supplied data. Stack overflow and heap overflow are the most common types of buffer overflow. Windows has patched almost all known and exploitable buffer overflow vulnerabilities and it is rare to see a new one discovered these days.
Other than patching the vulnerabilities in the software, Windows also developed some techniques to mitigate buffer overflows.
A Stack is a a very important data structure used in programming. It is used to store local variables and the function return address. Local variables can store user supplied data. As an example, HTTP server can store the HTTP request sent by the user in a variable. If the server does not check the size of the supplied HTTP request, it gets written to the stack where it can corrupt other data like the return address. The return address can be overwritten to redirect the control flow to a shellcode which is part of the user supplied variable value. A shellcode can pop a backdoor, launch a program or download another malware. Stack overflow exploitation works by overwriting the return address on the stack by a user supplied local variable.
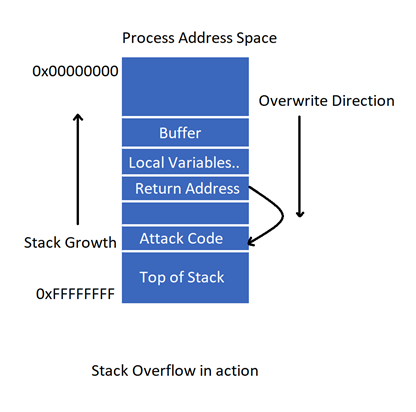 Windows came up a with stack canaries to detect overwriting of the return address. The stack canaries feature was implemented in Windows XP SP2. An exception was triggered when the return address was overwritten. Unfortunately, hackers bypassed this too using a technique called SEH Overwrite (Structured Exception Handler). The address of the exceptional handler needed to handle the return address overwrite exception was stored on the stack. Hence, the attacker was able to take control by overwriting this value.
Windows came up a with stack canaries to detect overwriting of the return address. The stack canaries feature was implemented in Windows XP SP2. An exception was triggered when the return address was overwritten. Unfortunately, hackers bypassed this too using a technique called SEH Overwrite (Structured Exception Handler). The address of the exceptional handler needed to handle the return address overwrite exception was stored on the stack. Hence, the attacker was able to take control by overwriting this value.
Heap overflow also worked in a similar manner. User supplied data was able to corrupt important data structures on the heap to take control of the program. To track heap allocation, linked lists are used. The pointers used to connect node in the linked list are corrupted and overwritten by user controlled code.
Windows invented a technique called DEP (Data Execution Prevention) to prevent this kind of exploitation. The technique imposed a restriction that anything on the stack or heap should be treated as data and should not be executed.
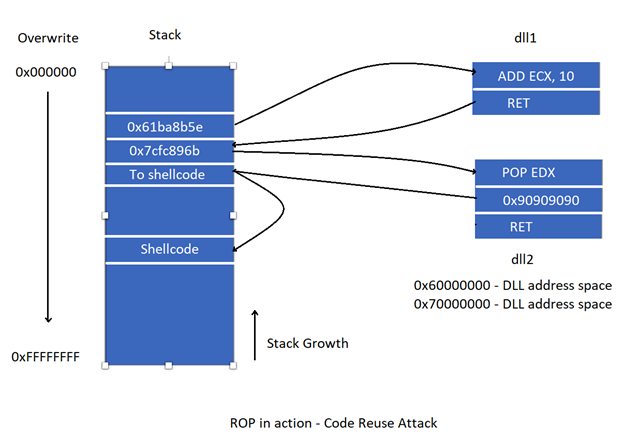
The shellcode is composed of addresses of instructions inside a DLL instead of only instructions. This technique is called ROP chain (return oriented programming). The ROP technique executes the code chunks that span across multiple DLLs to carry out the same functionality, which could have also been achieved by executing a contiguous chunk of shellcode placed in a heap or stack in absence of DEP. The code chunks from the DLLs used in ROP are called ROP gadgets. It was possible to create a ROP chain by using addresses inside a loaded DLL as the DLL addresses were fixed. To mitigate this ROP, Windows introduced another technique called ASLR (Address Space Layout Randomization). This technique randomized the base addresses of DLL with respect to the main executable each time the program started. This technique was quite effective with minimal flaws. The attacker used the non-randomized DLLs to create exploits. Attackers sometimes used another technique called information disclosure or information leak to find out the address of a DLL and then use the address in the exploit.
Now, stack and heap overflow are rarely seen in popular applications. It seems that most companies have done a good job on educating engineers about basic vulnerabilities. Use-After-Free has been the most recent popular vulnerability. It’s one of the most exploited vulnerabilities in the past five to six years.It was found in all browsers, Adobe Reader and Adobe Flash applications. Use-After-Free is a memory corruption vulnerability. The vulnerability is triggered when the program tries to access an object that has been freed. The object has been freed, but there was still a pointer that pointed to the memory location of the freed object. Trying to access the data pointed to the leads of the vulnerability. This kind of pointer is called a dangling pointer. Attackers can misuse the pointer to execute shellcode. Microsoft introduced a technique called isolated heap in mid-2014 to minimize use after free vulnerabilities. Isolated heap allocated separate heap for critical objects. The heap blocks are freed from user controlled data after the object is freed. Isolated heap helped to prevent exploitation of use-after-free vulnerabilities, but isolated heap was applied only to selective objects, not all objects. So, some objects might still be subject to risk. To further elevate the security, Microsoft added Protected Free or Deferred Free. In this technique, Microsoft does not free the object immediately. Instead, it frees it sometime later so that the attacker cannot predict the time when they can control the freed object.
Another very popular technique used to exploit browsers is heap spray. JavaScript used in browsers stores variables in the heap. The heap spray technique was used to fill the heap with lots of shellcode chunks. The advantage of this technique is that the attacker does not need to accurately predict the address of shellcode on heap. An address like 0xaaaaaaaa ,0xbbbbbbbbb is used, which most likely points to the heap and the shellcode would then probably lie around that. Chromium sandbox was one of Google Chrome’s innovations to counter all kinds of browser exploitation. Internet Explorer also came up with a similar solution.
But, still the DEP and ASLR was an issue. Hence, the novel technique JIT spray (Just In Time) was used. The technique was mostly used to exploit Flash-related vulnerabilities. JIT Engine is a native code generator, which is used by all modern browsers to speed up execution by parsing, optimizing and compiling bytecode to native code for the machine to run. The emitted code by JIT Engine is marked as executable in memory by default. This code can be sprayed into the heap by calculating the right size allocation of a page. After that, it’s a matter of jumping to a known heap address to get code execution bypassing DEP and ASLR all together. This bytecode can be generated in real time by JIT or it can be pre-generated and sent on the wire as a Flash/Java file on the internet. This technique was first used with Flash ActionScripts to spray heap, which used long XOR sequences to store shellcode and jumped onto a known heap address to get reliable code execution. After researchers were able to use the same JIT spray technique to exploit native JAVA and also used ASM.js recently for exploitation.
To keep up with the continuously evolving exploit landscape, Microsoft came up with EMET (Enhanced Mitigation Experience Toolkit) in 2009. It is an added layer of defense against code reuse attacks like ROP and provides better protection against Heap and JIT spray. Though it has to be manually installed by an administrator. Since EMET was not designed as an integral part of the OS, the exploit writers were able to bypass/disable EMET and achieve code execution in each of its versions. Though EMET led many security innovation in Windows product lines 7, 8 ,8.1, 10 and it’s Linux counterparts. As underlying OS changed, Microsoft decided to build in this security in OS as Windows Defender Exploit Guard, which will support future Windows versions after Windows 10, with many improvements. Microsoft decided to end life support for EMET. The latest version will be EOL’d on July 31, 2018.
CONCLUSION
Exploitation and Anti-Exploitation techniques is almost a cat and rat race. Security professionals always come up with an idea to combat Cyber criminals but at the same time criminals figure out a way to defeat it. Juniper Advanced threat detection product detects exploits to keep the customers safe.


