Nearly everything we do on the network involves applications, from web browsing and chat to mobile games and services that allow us to get work done. Applications store, process and exchange data, which enables us to connect to each other and makes our digital lives easier. And when we use them, we need them to be accessible right away, and we trust that they will do only what they were intended to do — that is, we trust that our application experience is secure. As such, application security is a core tenet of the Juniper Experience-First Networking philosophy.
When application code is written, however, it sometimes contains errors which present opportunities that attackers can use to exploit the underlying resources and process — or workloads — that power the application, such as databases and data collectors. Just look at the latest public breaches – most, if not all, of them involve the successful exploitation of one or more application vulnerabilities.
Organizations may not even be aware that certain application vulnerabilities exist until it’s too late. As much as every organization tries to adhere to a secure software development lifecycle (SDLC) to build secure applications from the start, there’s always the potential for risk. This means there will always be vulnerabilities that attackers can exploit. But what if organizations had a safety net to protect application workloads against exploits, including zero-days?
Meet Juniper Cloud Workload Protection
Today, we’re thrilled to announce Juniper Cloud Workload Protection to automatically defend application workloads in any cloud or on-premises data center environment against application exploits as they happen, including the Open Web Application Security Project® (OWASP) Top 10 and memory-based attacks.
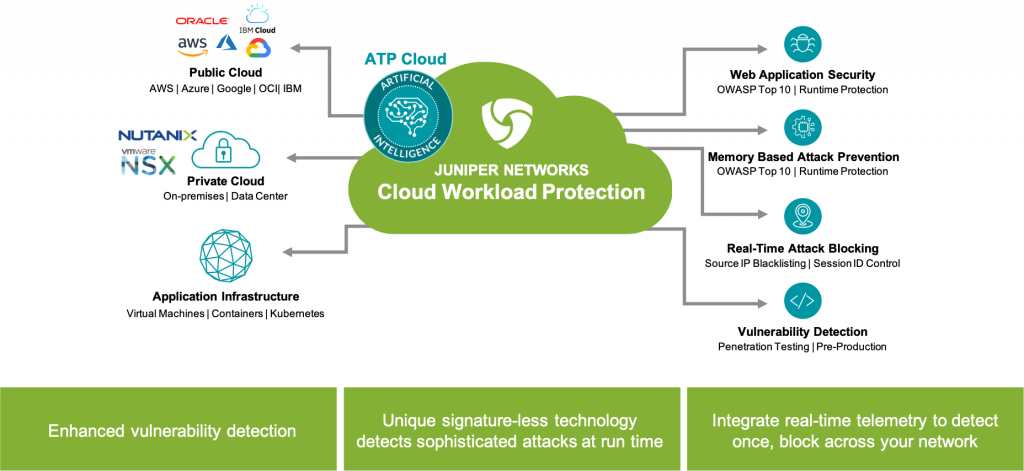
Juniper Cloud Workload Protection
Juniper Cloud Workload Protection is a lightweight software agent that controls application execution and monitors the application’s behavior and context – what it’s supposed to do against what’s happening in real-time. Vulnerability remediation is done automatically without admin intervention. Juniper Cloud Workload Protection ensures that production applications always have a safety net against vulnerability exploits, keeping business-critical services connected and protected. This new Juniper product provides the following critical capabilities:
- Signatureless Run-Time Application Self-Protection (RASP) provides real-time protection against attacks. It protects the application from malicious actions, such as exploitation and data theft, without any manual intervention, catching sophisticated attacks that endpoint detection (EDR) and web application firewall (WAF) solutions cannot.
- Memory-Based Attack Prevention provides real-time protection against advanced memory-based attacks, including fileless, return-oriented programming (ROP) and buffer overflow attacks.
- Vulnerability Detection continuously assesses vulnerabilities in applications and containers to detect serious and critical exploit attempts as they happen. Juniper Cloud Workload Protection delivers information on the exploit attempt to DevSecOps teams to better understand where the vulnerability exists, so they can remediate.
- Comprehensive Telemetry provides rich application-level security event generation and reporting, including application connectivity, topology and detailed information about the attempted attack.
- Optimized Control Flow Integrity (OCFI) technology minimizes false alerts by validating the execution of applications and detecting attacks without using behavior or signatures.
- Zero Trust Microsegmentation shields application resources from lateral threat propagation and integrates with Juniper vSRX Virtualized Firewalls to restrict access based on risk, even as workloads and virtual environments change. Automated threat response with built-in, real-time telemetry helps security teams detect threats once and block them across the entire network.
Juniper Cloud Workload Protection continues the drumbeat of Juniper Connected Security by supporting every type of workload and providing a safety net for applications. Customers no longer need to trade-off between limiting their risk of a data breach or missing release deadlines, especially those in production.
Organizations can keep applications connected and protected, providing application teams the means to deliver, operate and ensure that their data center environments are following compliance rules while continuously looking out for anomalies.
Strengthening Zero Trust Data Center Architecture
Juniper Cloud Workload Protection is the newest part of Zero Trust data center architecture. Our world-class data center networking solutions and Connected Security strategy connect and orchestrate application infrastructure across multiple data center environments and secure every point of connection along the way, from the DC gateway to the interconnect, between servers and within application workloads.
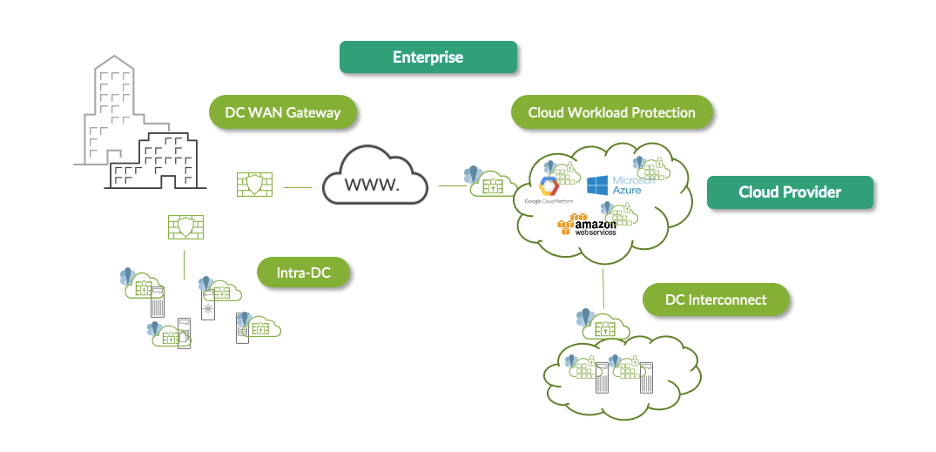
The Zero Trust Data Center: Securing the DC WAN Gateway, Intra-DC, DC Interconnect and Application Workloads
Juniper Connected Security is based on the premise that networking and security must converge, on-premises and in the cloud, securing data transactions from client to workload. Visibility, intelligence and enforcement must extend to every point of connection on the network to effectively safeguard users, applications and infrastructure. That’s what Juniper Cloud Workload Protection and the Zero Trust data center architecture deliver, connecting and protecting applications in any cloud while ensuring great user experiences.
Attending Black Hat 2021? Come see us!
Additional Resources
- Juniper Cloud Workload Protection Product Page
- Protect your Zero Trust Data Center Infographic
- Juniper Cloud Workload Protection Demonstration
- Webinar: Automating and Securing Your Zero Trust Data Center
- Juniper Cloud Workload Protection Datasheet
- Podcast: Introducing Juniper Cloud Workload Protection


